Admin Token
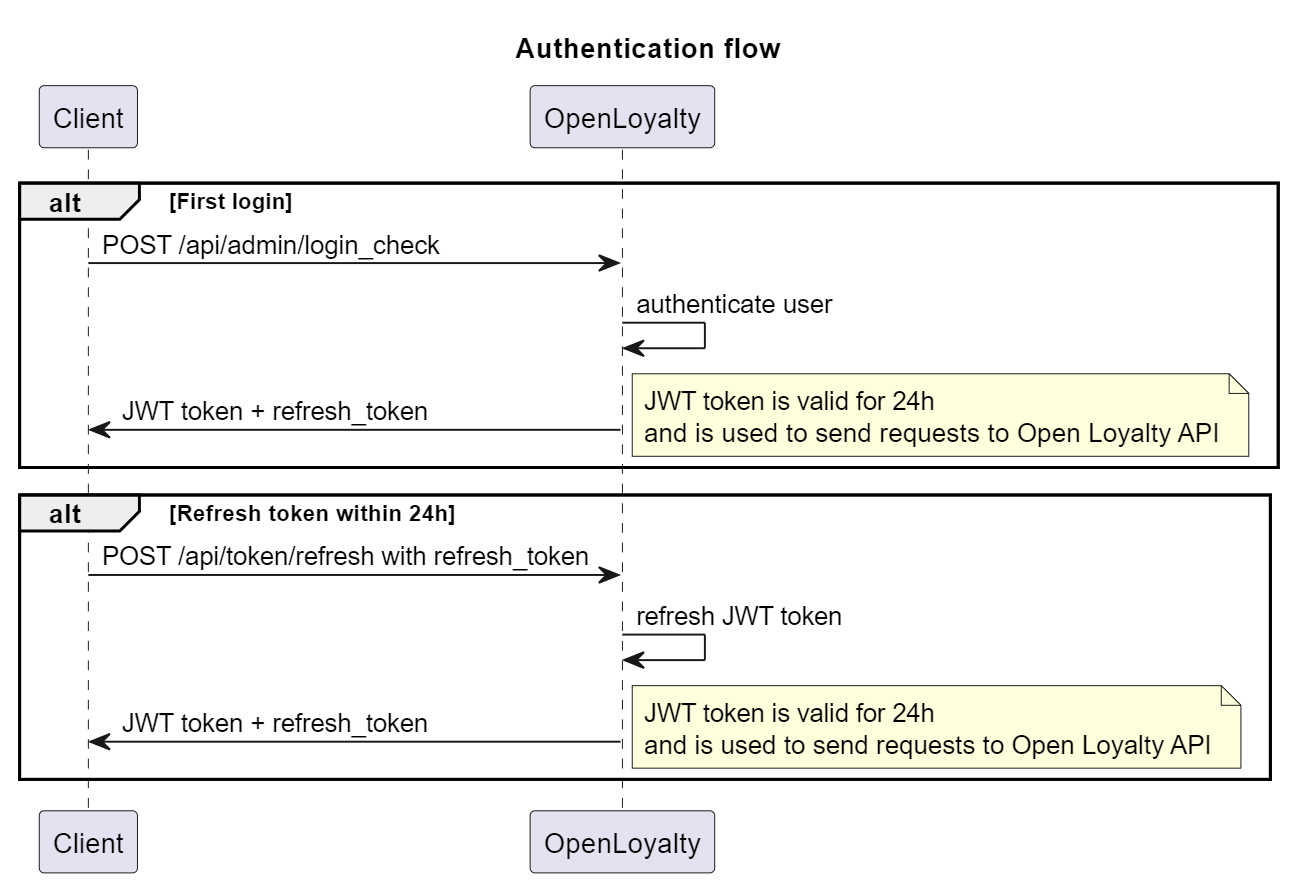
Securing your application with OpenLoyalty starts with a robust authentication flow. OpenLoyalty leverages JSON Web Tokens (JWT) to ensure that requests to its API are authorized.
Initial Admin Login
{
"username": "[email protected]",
"password": "password123"
}{
"token": "eyJhbGciOiJSUzI1NiIsInR5cCI...",
"refresh_token": "def50200a2e8c9a2..."
}Maintaining Authentication State
Best Practices
Last updated
Was this helpful?

